In a recent cybersecurity development, threat actors have been leveraging an undocumented Google OAuth endpoint named “MultiLogin” to compromise user accounts by reviving expired authentication cookies. This sophisticated attack allows cybercriminals to gain unauthorized access to Google accounts even after users have taken security measures such as logging out, resetting passwords, or when their sessions have expired. This article delves into the details of this zero-day exploit, shedding light on how it works, its scale of exploitation, and the subsequent adoption by multiple information-stealing malware families.
The Zero-Day Exploit Unveiled
The exploit came to public attention when a threat actor named PRISMA disclosed their discovery on October 20, 2023, through a post on Telegram. PRISMA claimed to have found a way to restore expired Google authentication cookies, which are crucial for maintaining persistent access to compromised accounts. Subsequent reverse engineering of the exploit by cybersecurity researchers at CloudSEK revealed the utilization of the “MultiLogin” endpoint within the Google OAuth framework.
Understanding the MultiLogin Endpoint
The MultiLogin endpoint, as per the Google Chrome source code, is intended for synchronizing accounts across different Google services. It accepts a vector of account IDs and auth-login tokens to set Chrome accounts in the browser’s Google authentication cookies for various Google websites, including but not limited to YouTube. The endpoint is part of the Gaia Auth API and is triggered when accounts in cookies are inconsistent with accounts in the browser.
The Anatomy of the Attack
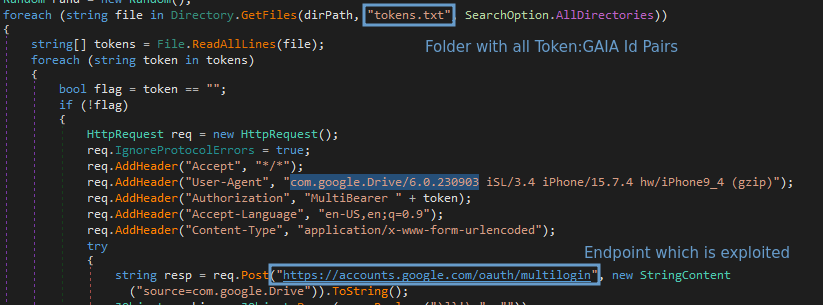
CloudSEK researchers discovered that the information-stealing malware exploiting the MultiLogin endpoint extracts tokens and account IDs associated with Chrome profiles logged into a Google account. This pilfered information contains two critical components: the service (GAIA ID) and encrypted_token. The encrypted tokens are then decrypted using an encryption stored in Chrome’s ‘Local State’ file. Remarkably, this encryption key is the same one used to decrypt saved passwords in the browser.

Source: CloudSEK
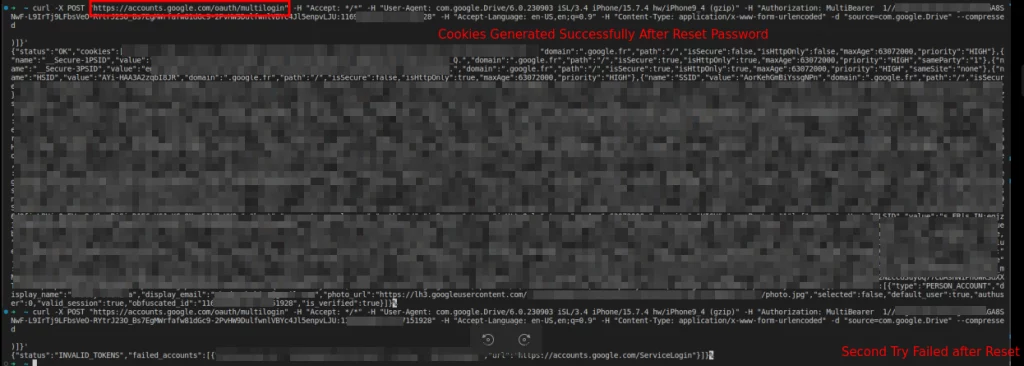
Using the stolen token:GAIA pairs, threat actors can generate requests to the MultiLogin endpoint, thereby regenerating expired Google Service cookies. This process enables cybercriminals to maintain persistent access to compromised accounts, even after users have taken actions such as resetting their passwords. Notably, CloudSEK researchers were able to successfully regenerate expired Google authentication cookies through the reverse-engineered exploit.

Source: CloudSEK
Malware Adoption and Blackboxing Techniques
The Lumma stealer was among the first to adopt this exploit on November 14, 2023. In an attempt to protect their newfound capability, developers of Lumma applied blackboxing techniques, encrypting the token:GAIA pair with private keys to conceal the mechanism from competitors and prevent replication of the feature. However, despite these efforts, other malware developers managed to copy the feature, and Rhadamanthys became the first to follow suit on November 17.
Subsequent Developments and Exploitation Proliferation
Following Lumma and Rhadamanthys, several other information stealers have rapidly adopted the exploit. Notable instances include Stealc on December 1, Medusa on December 11, RisePro on December 12, and Whitesnake on December 26. At least six information-stealing malware families currently claim the ability to regenerate Google cookies using the MultiLogin API endpoint.
A video released by threat intelligence firm Hudson Rock on YouTube further demonstrates how a cybercriminal can exploit this cookie restoration technique. The ease with which the exploit can be demonstrated raises concerns about the potential widespread impact of this vulnerability.
Google’s Response and Mitigation Efforts
BleepingComputer reported that they contacted Google multiple times over a month with inquiries regarding these claims and sought information on how the tech giant plans to mitigate the issue. As of the reporting, there has been no response from Google. The absence of an official statement from Google raises questions about the company’s awareness of the actively exploited zero-day flaw and its current mitigation efforts.
Lumma’s Attempt to Counteract Google’s Mitigations
An intriguing development in this ongoing saga is Lumma’s update to counteract Google’s mitigations. This suggests that Google may be actively addressing the issue, prompting malware developers to adapt their tactics. Lumma, in response to Google’s measures, turned to using SOCKS proxies to evade Google’s abuse detection measures. Additionally, encrypted communication between the malware and the MultiLogin endpoint was implemented to further obscure the malicious activity.
Uncertainty Surrounding Mitigation Status
Despite Lumma’s attempts to circumvent Google’s mitigations, the exact status of the exploitation and Google’s countermeasures remains uncertain. The lack of official confirmation from Google regarding the abuse of the MultiLogin endpoint adds to the ambiguity surrounding the situation. Cybersecurity experts are closely monitoring the developments, emphasizing the importance of timely and transparent communication from service providers when addressing such vulnerabilities.

